The Intelligence Lifecycle: Phase 4 - Analysis

Last time we walked through Phase 3: Processing. I shared how Processing is more like the preparing of ingredients right before you start cooking. If you haven't read Phase 1, Phase 2 or Phase 3, I recommend starting there to better understand the process in its entirety. Now, it's time for Phase 4: Analysis.
Phase 4: Analysis
In this stage, all the clues come together. Analysis is the deliberate process of studying what you've gathered, comparing details, and piecing them into a clear picture. The result is an intelligence product: a report, briefing, estimate or visual, that others can act on.
(Adapted from Baker & Henderson, 2017)
What does this mean for you?
Analysis is all about giving your data purpose. This is where you stop collecting and start thinking. Connect the dots, spot the patterns, and uncover what the information actually says.
Please be aware that these are examples, and depending on your position and daily job tasks, Processing may look slightly different.
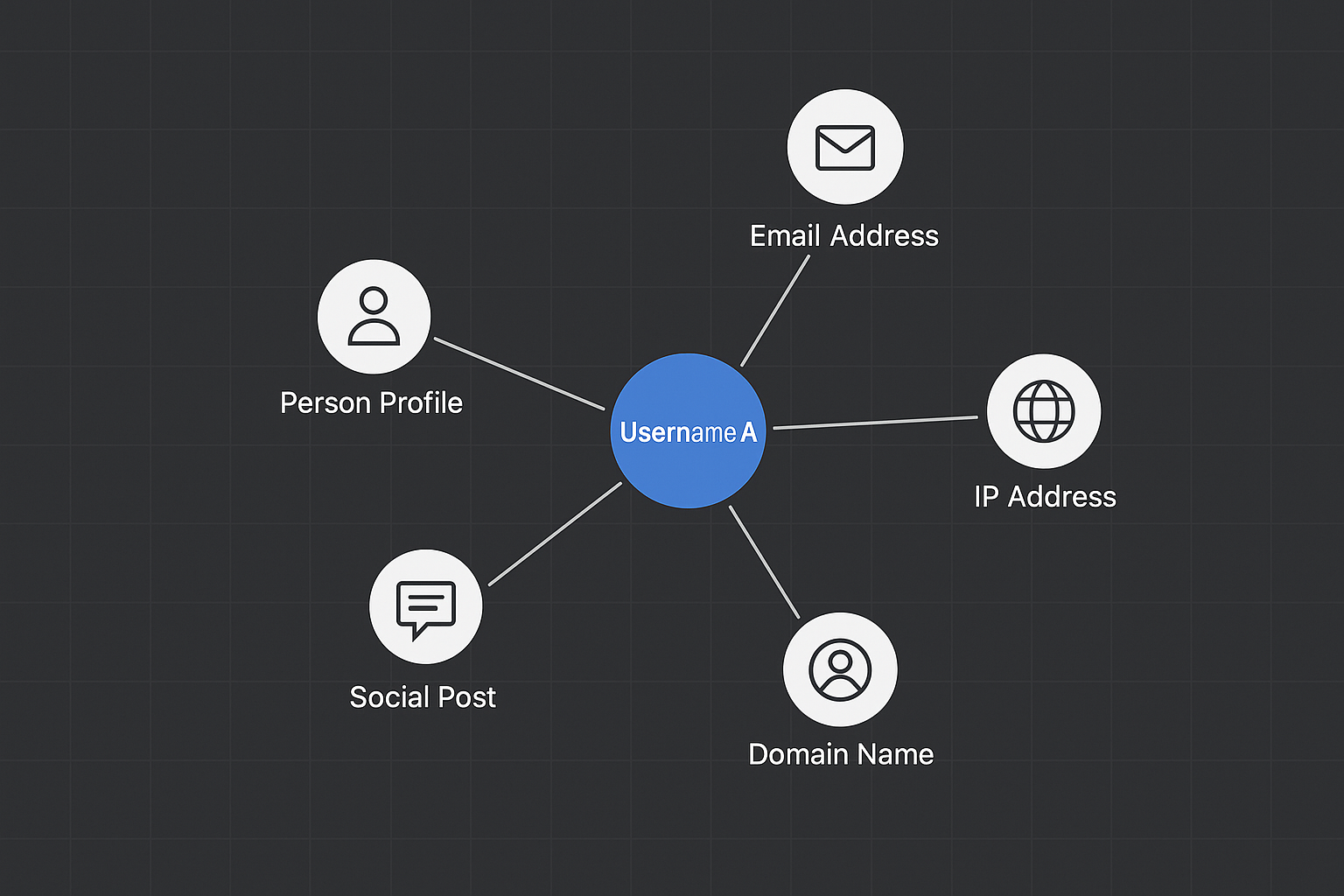
- Look for patterns: Identify trends, relationships, or inconsistencies across your findings. (visuals are good for this)
- Verify accuracy: Cross-check information, confirm credibility, and question assumptions. (something as small as misreading something can hurt your final report.)
- Connect information: Merge data from different platforms, timelines, or sources to see the bigger picture.
- Visualize it: Create charts, timelines, or link diagrams to make insights easier to understand. (One of my favorite)
- Assess significance: Focus on what truly matters to your objective or client. (Don't waste time chasing some irreverent lead)
- Document: Record how you reached your conclusions, including evidence and limitations.
Think of it like cooking the meal: Collection was grocery shopping, Processing was prepping the ingredients, and Analysis is when you finally start to cook.
(Now we're really cooking!)
Do analysts always do this?
Nope.
Not every analyst reaches this phase and that's completely normal. The intelligence lifecycle often overlaps across different roles. Some people focus on collection and processing, while others handle analysis and reporting. It depends on the mission, the tools available, and the scope of the investigation.
If you're part of a larger team, you might hand off your findings to an analyst who specializes in deeper review or trend analysis. If you're a solo investigator, you might carry the process all the way through yourself. Regardless, understanding what happens in this phase helps you recognize how your work fits into the bigger picture.
This phase will play out differently across fields. For example, in CTI, analysts use data from logs, IOCs, and threat feeds to identify attack patterns, assess intent, and produce reports that help organizations strengthen defenses or respond to incidents. In investigative OSINT, analysis might involve linking identities, mapping digital footprints, or spotting behavioral trends across platforms. The focus may change but the reasoning and critical thinking stays the same.
Personally, I enjoy this stage because it demands more critical thinking. It's where you stop simply gathering information and start interpreting it. You're not just looking at what you found, but how it answers the question or the purpose of the investigation.
💭 I’m curious…
How do you approach analysis? Do you prefer to visualize your findings with charts and link maps or do you lean toward detailed written reports? What helps you make sense of complex data and where do you find the biggest challenge in connecting it all together?
👀 Your turn
I’d love to hear how you approach this phase. Drop your thoughts in the comments below, or share your process on social media and tag me so we can keep the conversation going. The more we exchange ideas, the more we all grow as analysts!
#osint #intelligenceanalysis #investigations #digitalinvestigations




